A Small Utility To Deal With Malware Embedded Hashes
Uchihash is a handy tool that can assist malware analysts in saving time by eliminating the need to handle embedded hash values, which are utilized for a variety of purposes such as:
- Dynamically importing APIs (especially in shellcode)
- Checking running process used by analysts (Anti-Analysis)
- Checking VM or Antivirus artifacts (Anti-Analysis)
With Uchihash, you have the ability to create hashes using your personalized hashing algorithm, explore a pre-generated hashmap for a collection of hashes, and even generate an IDAPython script that simplifies analysis by annotating the hashes with their respective values.
Installation
1
git clone https://github.com/N1ght-W0lf/Uchihash.git
1
pip install -r requirements.txt
Usage
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
usage: uchihash.py [-h] [--algo ALGO] [--apis] [--keywords] [--list LIST] [--script SCRIPT] [--search SEARCH] [--hashes HASHES] [--ida]
optional arguments:
-h, --help show this help message and exit
--algo ALGO Hashing algorithm
--apis Calculate hashes of APIs
--keywords Calculate hashes of keywords
--list LIST Calculate hashes of your own word list
--script SCRIPT Script file containing your custom hashing algorithm
--search SEARCH Search a JSON File containing hashes mapped to words
--hashes HASHES File containing list of hashes to search for
--ida Generate an IDAPython script to annotate hash values
Examples:
* python uchihash.py --algo crc32 --apis
* python uchihash.py --algo murmur3 --list mywords.txt
* python uchihash.py --search hashmap.txt --hashes myhashes.txt
Notes
--algo: One of the available hashing algorithms--apis: Hashes a huge list of windows APIs--keywords: Hashes a list of common keywords used by malware families such as Analysis tools and VM/Antivirus/EDR artifacts (see data/keywords_list.txt)--list: Words are separated by a newline--script:Hashing function must be called hashme() and the return value must be in hex format 0xDEADBEEF--search: File to search must be in JSON format--hashes: Hash values are separated by a newline and they must be in hex format
Available Hashing Algorithms
- md4
- md5
- sha1
- sha224
- sha384
- sha512
- ripemd160
- whirlpool
- crc8
- crc16
- crc32
- crc64
- djb2
- sdbm
- loselose
- fnv1_32
- fnv1a_32
- fnv1_64
- fnv1a_64
- murmur
Example
An example using a real malware family would be BuerLoader, which utilizes hash values for dynamically importing APIs and employs a custom hashing algorithm.
To begin, we must first implement the custom hashing algorithm in Python.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
def ROR4(val, bits, bit_size=32):
return ((val & (2 ** bit_size - 1)) >> bits % bit_size) | \
(val << (bit_size - (bits % bit_size)) & (2 ** bit_size - 1))
def hashme(s):
res = 0
for c in s:
v3 = ROR4(res, 13)
v4 = c - 32
if c < 97:
v4 = c
res = v4 + v3
return hex(res)
```
Next, we compute the hashes for all APIs.
```bash
python uchihash.py --script custom_algo.py --apis
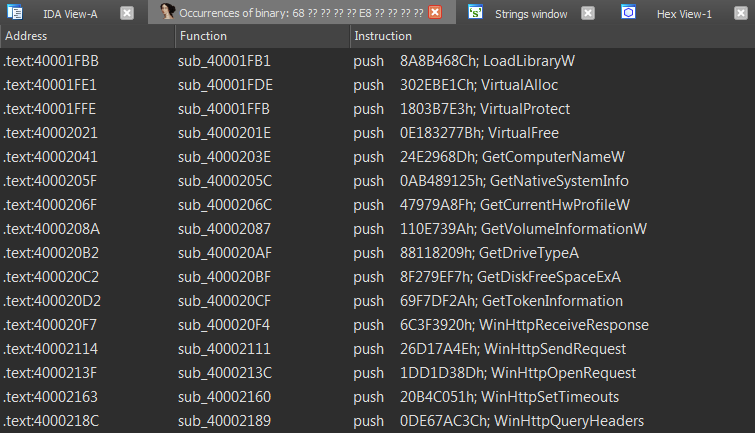
Ultimately, our goal is to locate the hash values employed by BuerLoader within the generated hashmap. Additionally, we can produce an IDAPython script to label these hash values with their respective API names.
1
python uchihash.py --search output/hashmap.txt --hashes buer_hashes.txt --ida
We should get 2 output files, one is “output/search_hashmap.txt” which maps BuerLoader’s hash values to API names:
1
2
3
4
5
6
7
8
9
{
"0x8a8b468c": "LoadLibraryW",
"0x302ebe1c": "VirtualAlloc",
"0x1803b7e3": "VirtualProtect",
"0xe183277b": "VirtualFree",
"0x24e2968d": "GetComputerNameW",
"0xab489125": "GetNativeSystemInfo",
.......
}
The other file is “output/ida_script.py” which will add the comments to your idb:
⚠ ONLY USE FOR EDUCATIONAL PURPOSES ⚠