Web Browsers are useless here
Welcome.
Good Luck
-3301
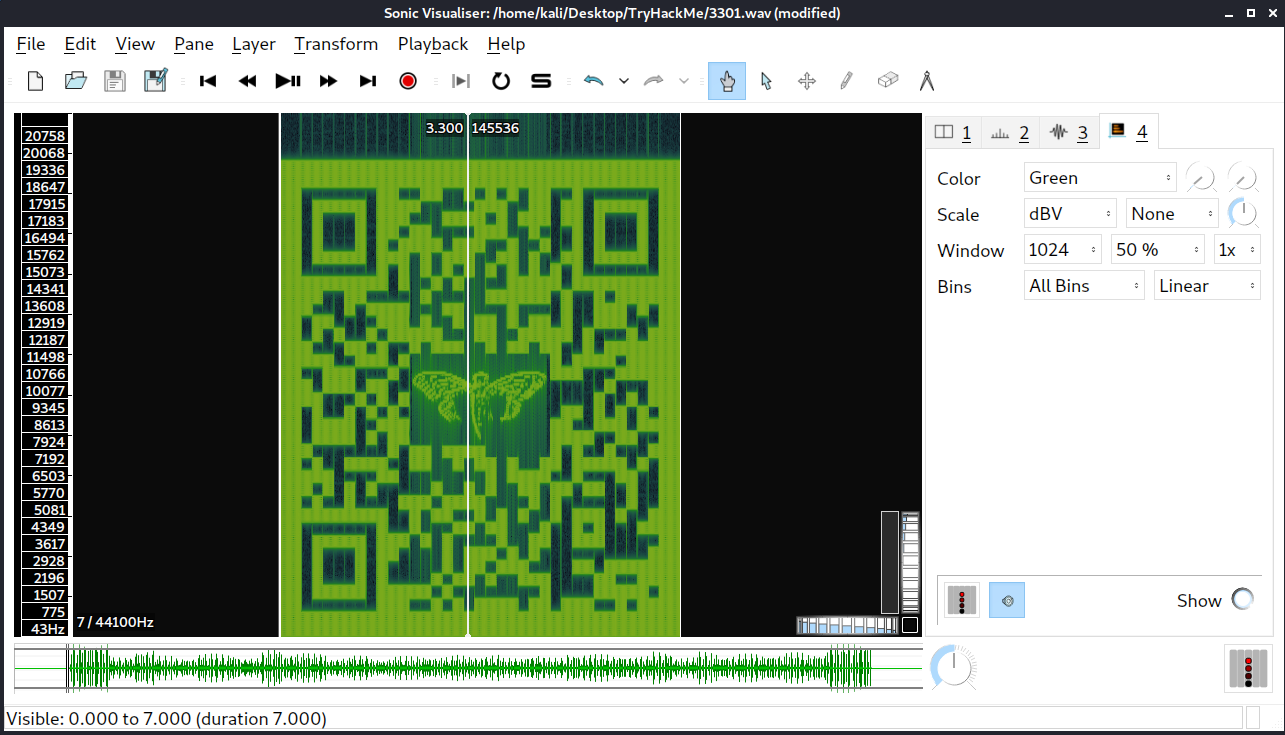
Analyze The Audio
1. What is the link inside of the audio?
1
https://pastebin.com/wphPq0Aa
Use various encryption methods and ciphers to decode the passphrase and access the metadata of Welcome.jpg
Decode the Passphrase
1. Find and Decrypt the passphrase and key
1
No answer needed
2. What is the decrypted passphrase?
Passphrase: SG01Ul80X1A0NTVtaHA0NTMh
Key: Q2ljYWRh
| ❯ echo SG01Ul80X1A0NTVtaHA0NTMh | base64 -d |
1
Hm5R_4_P455mhp453!%
3. What is the decrypted key?
| ❯ echo Q2ljYWRh | base64 -d |
1
Cicada
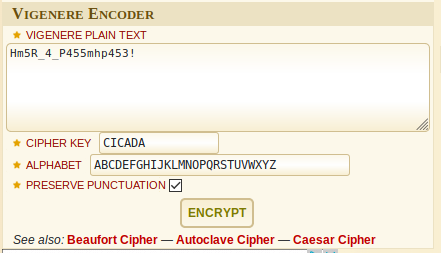
4. Still looks funny? Find and use a cipher along with the key to decipher the passphrase
1
No answer needed
5. What is the final passphrase
1
Ju5T_4_P455phr453!
Gather Metadata
Use Steganography tools to gather metadata from Welcome.jpg as well as find the hidden message inside of the image file
1. Using the found passphrase along with Stego tools find the secret message
Click to show Answer
2. What link is given?
Click to show Answer
1
https://imgur.com/a/c0ZSZga
I am surprised you have made it this far…
I doubt you will make it any further.
-3301
Use Stego tools to find the hidden files inside of the image
https://github.com/crorvick/outguess
Find Hidden Files
1. Using stego tools find the hidden file inside of the image
Click to show Answer
2. What tool did you use to find the hidden file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
➜ TryHackMe outguess -r 8S8OaQw.jpg bope
Reading 8S8OaQw.jpg....
Extracting usable bits: 29035 bits
Steg retrieve: seed: 38, len: 1351
➜ TryHackMe cat bope
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA1
Welcome again.
Here is a book code. To find the book, break this hash:
b6a233fb9b2d8772b636ab581169b58c98bd4b8df25e452911ef75561df649edc8852846e81837136840f3aa453e83d86323082d5b6002a16bc20c1560828348
I:1:6
I:2:15
I:3:26
I:5:4
I:6:15
I:10:26
/
/
I:13:5
I:13:1
I:14:7
I:3:29
I:19:8
I:22:25
/
I:23:-1
I:19:-1
I:2:21
I:5:9
I:24:-2
I:22:1
I:38:1
Good luck.
3301
-----BEGIN PGP SIGNATURE-----
Version: GnuPG v1.4.11 (GNU/Linux)
iQIcBAEBAgAGBQJQ5QoZAAoJEBgfAeV6NQkPf2IQAKWgwI5EC33Hzje+YfeaLf6m
sLKjpc2Go98BWGReikDLS4PpkjX962L4Q3TZyzGenjJSUAEcyoHVINbqvK1sMvE5
9lBPmsdBMDPreA8oAZ3cbwtI3QuOFi3tY2qI5sJ7GSfUgiuI6FVVYTU/iXhXbHtL
boY4Sql5y7GaZ65cmH0eA6/418d9KL3Qq3qkTcM/tRAHhOZFMZfT42nsbcvZ2sWi
YyrAT5C+gs53YhODxEY0T9M2fam5AgUIWrMQa3oTRHSoNAefrDuOE7YtPy40j7kk
5/5RztmAzeEdRd8QS1ktHMezXEhdDP/DEdIJCLT5eA27VnTY4+x1Ag9tsDFuitY4
2kEaVtCrf/36JAAwEcwOg2B/stdjXe10RHFStY0N9wQdReW3yAOBohvtOubicbYY
mSCS1Bx91z7uYOo2QwtRaxNs69beSSy+oWBef4uTir8Q6WmgJpmzgmeG7ttEHquj
69CLSOWOm6Yc6qixsZy7ZkYDrSVrPwpAZdEXip7OHST5QE/Rd1M8RWCOODba16Lu
URKvgl0/nZumrPQYbB1roxAaCMtlMoIOvwcyldO0iOQ/2iD4Y0L4sTL7ojq2UYwX
bCotrhYv1srzBIOh+8vuBhV9ROnf/gab4tJII063EmztkBJ+HLfst0qZFAPHQG22
41kaNgYIYeikTrweFqSK
=Ybd6
-----END PGP SIGNATURE-----
➜ TryHackMe
1
outguess
Book Cipher
We have one last challenge to find our individuals
Find the last clue, crack the hash, decipher the message
Good Luck
-3301
Use Hash cracking tools to reveal the text to the text
Use methods like Cicada to decipher the message
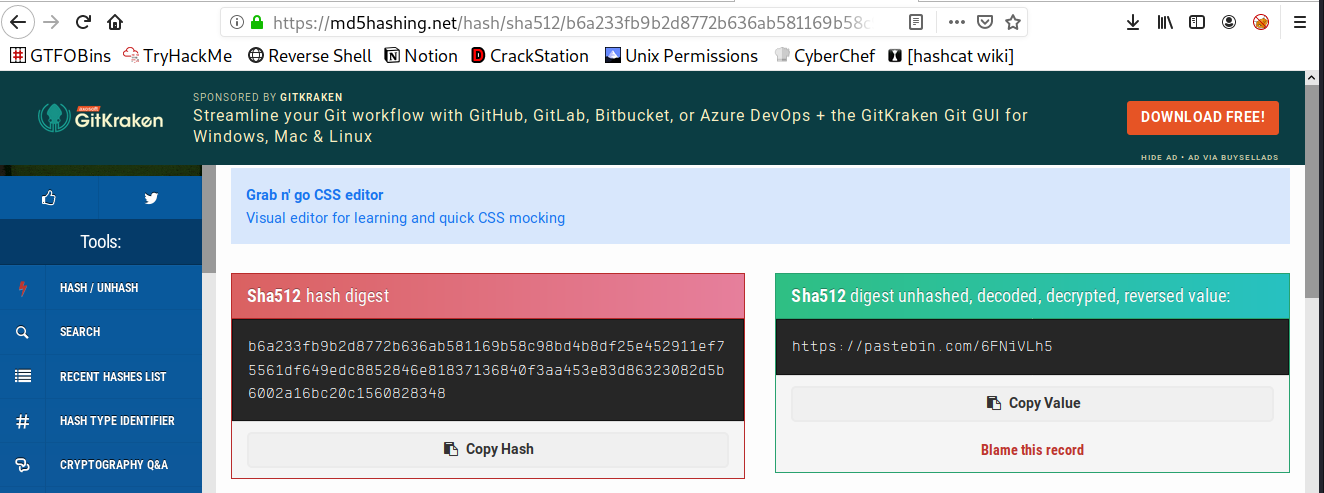
Hash sha512: b6a233fb9b2d8772b636ab581169b58c98bd4b8df25e452911e
1. Crack the Hash
1
No answer needed
2. What is the Hash type?
1
No answer needed
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
➜ TryHackMe hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
HASH: b6a233fb9b2d8772b636ab581169b58c98bd4b8df25e452911ef75561df649edc8852846e81837136840f3aa453e83d86323082d5b6002a16bc20c1560828348
Possible Hashs:
[+] SHA-512
[+] Whirlpool
Least Possible Hashs:
[+] SHA-512(HMAC)
[+] Whirlpool(HMAC)
1
SHA512
3. What is the Link from the hash?
1
https://pastebin.com/6FNiVLh5
4. Decipher the message
1
No answer needed
5. What is the link?
For this response its a bit tricky to find out, the fist number is equal to the number on the paste-bin and the second one is for the number of the character on the line
1
https://bit.ly/39pw2NH
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
https://pastebin.com/raw/6FNiVLh5 # The paste-bin decoded before
I:1:6 = h # Exemple = Number 1, character number 6
I:2:15 = t
I:3:26 = t
I:5:4 = p
I:6:15 = s
I:10:26 = :
/ = /
/ = /
I:13:5 = b
I:13:1 = i
I:14:7 = t
I:3:29 = .
I:19:8 = l
I:22:25 = y
/ = /
I:23:-1 = 3
I:19:-1 = 9
I:2:21 = p
I:5:9 = w
I:24:-2 = 2
I:22:1 = N
I:38:1 = H
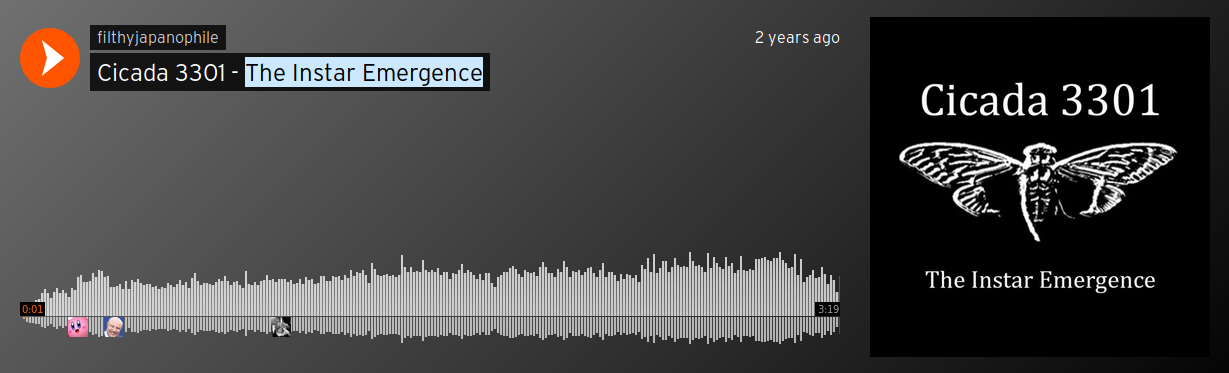
The Final Song
We have found the individuals we sought
-3301
SoundCloud Downloader
1. What is the song linked?
1
The Instar Emergence
Completed. Congratulation!