This room aims towards helping everyone learn about the basics of Malware Reverse Engineering.
These challenges are aimed towards learning about the “Static Analysis” technique used to analyze the malware. The main aim for this room is not to used any types of debuggers neither the executable’s/programs should be run on any platform. You are required to answer all the questions without even using the debugger and even not executing the executable’s/programs.
Meanwhile all the credits goes to @MalwareTechBlog for creating these awesome challenges.
Strings :: Challenge 1
This executable prints an MD5 Hash on the screen when executed. Can you grab the exact flag?
Note: You don’t need to run the executable!
1. What is the flag of which that MD5 gets generated? Let’s start reverse engineering the first flag by launching IDA
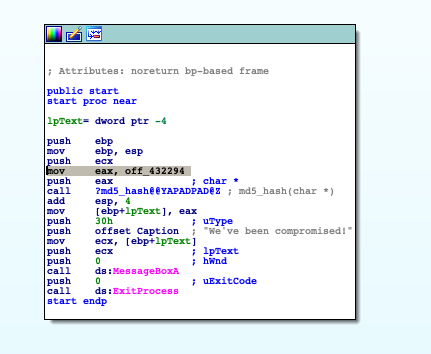
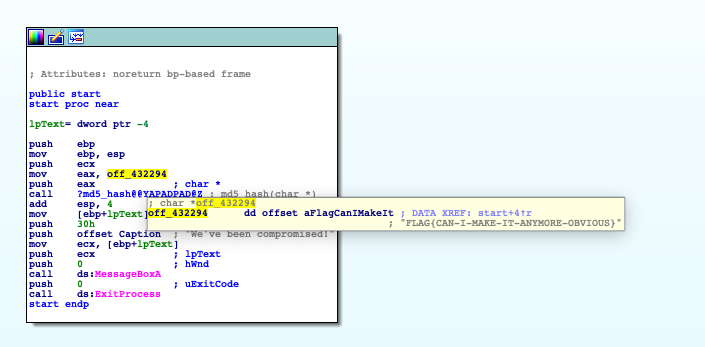
As you can see the command mov eax, off_432294 copies the content of the flag of the memory address (off_432294) into the EAX register.
You can see the flag by mouse over the address.
1
FLAG{CAN-I-MAKE-IT-ANYMORE-OBVIOUS}
Strings :: Challenge 2
This executable prints an MD5 Hash on the screen when executed. Can you grab the exact flag?
Note: You don’t need to run the executable!
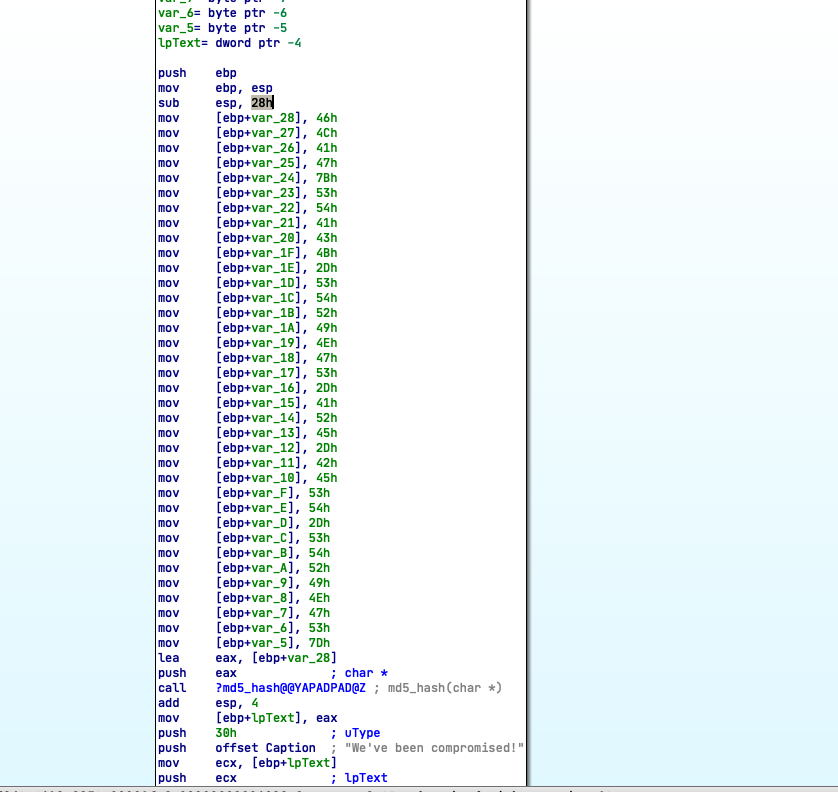
1. What is the flag of which that MD5 gets generated? Like the first one, let’s start the reverse with IDA
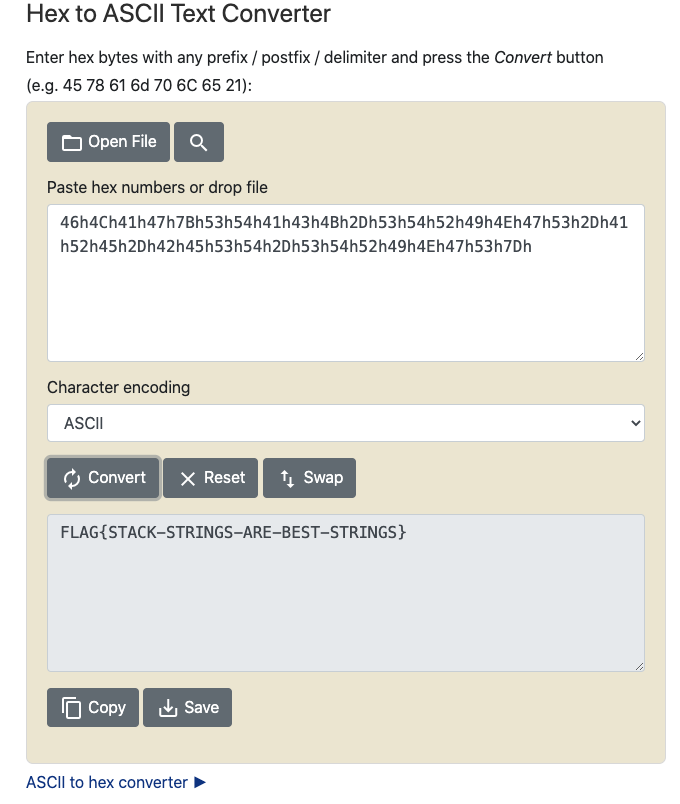
Well this one is pretty straight forward , you just need to decode the hex values into ascii.
1
FLAG{STACK-STRINGS-ARE-BEST-STRINGS}
Strings 3 :: Challenge 3
This executable prints an MD5 Hash on the screen when executed. Can you grab the exact flag?
Note: You don’t need to run the executable!
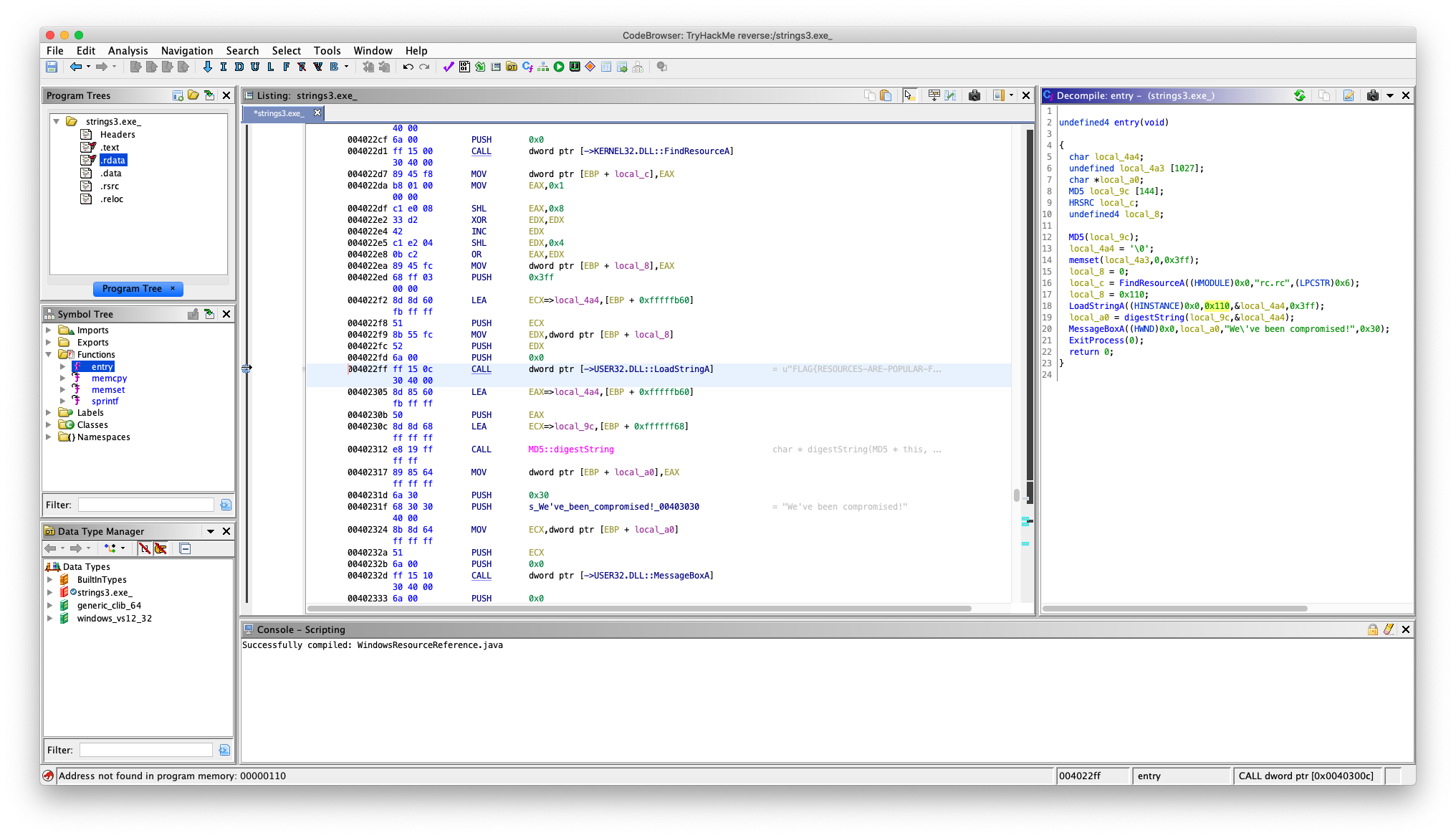
1. What is the flag of which that MD5 gets generated? For this one use GHIDRA and follow the image bellow 🙄
1
FLAG{RESOURCES-ARE-POPULAR-FOR-MALWARE}
Completed. Congratulation!